The Cactus Media API is a rpc API. You can find the Cactus Media API portal / hompage here. If you need Cactus Media API support, you can contact the support team directly at advertising@cactusmedia.com. For more information, check out their API Documentation. The Cactus Media API is not currently available on the RapidAPI marketplace.
Click "Request this API on RapidAPI" to let us know if you would like to access to this API.
Meanwhile, you can check out the top APIs that currently available for developers.
Related Articles
Related Cactus Media API Articles
![OpenAI bans ChatGPT accounts linked to Russian, Chinese cyber ops - RapidAPI]()
OpenAI bans ChatGPT accounts linked to Russian, Chinese cyber opsOpenAI banned ChatGPT accounts tied to Russian and Chinese hackers using the tool for malware, social media abuse, and U.S. satellite tech research. OpenAI banned ChatGPT accounts that were used by Russian-speaking threat actors and two Chinese nation-state a…
![Meta stopped covert operations from Iran, China, and Romania spreading propaganda - RapidAPI]()
Meta stopped covert operations from Iran, China, and Romania spreading propagandaMeta stopped three covert operations from Iran, China, and Romania using fake accounts to spread propaganda on social media platforms. Meta announced the disruption of three influence operations from Iran, China, and Romania using fake accounts to spread prop…
![Two flaws in vBulletin forum software are under attack - RapidAPI]()
Two flaws in vBulletin forum software are under attackExperts found two vulnerabilities in the vBulletin forum software, one of which is already being exploited in real-world attacks. Two critical vBulletin flaws, tracked as CVE-2025-48827 and CVE-2025-48828, enable API abuse and remote code execution. The exper…
![China-linked threat actor targeted +70 orgs worldwide, SentinelOne warns - RapidAPI]()
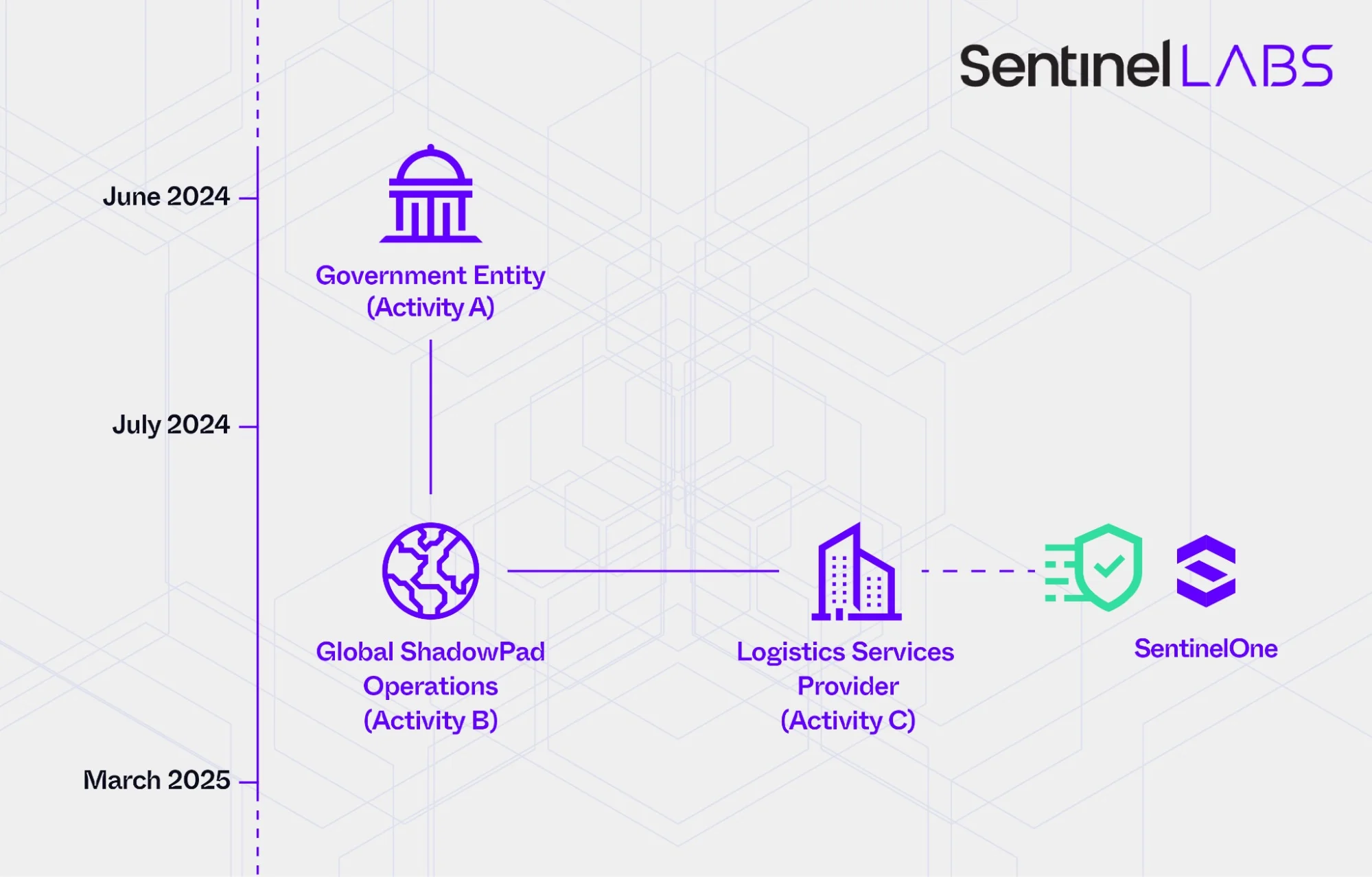
China-linked threat actor targeted +70 orgs worldwide, SentinelOne warnsChina-linked threat actor targeted over 70 global organizations, including governments and media, in cyber-espionage attacks from July 2024 to March 2025. In April 2025, cybersecurity firm SentinelOne warned that a China-linked threat actor, tracked as Purple…
![HPE fixed multiple flaws in its StoreOnce software - RapidAPI]()
HPE fixed multiple flaws in its StoreOnce softwareHewlett Packard Enterprise (HPE) addressed multiple flaws in its StoreOnce data backup and deduplication solution. HPE has released security patches for eight vulnerabilities in its StoreOnce backup solution. These issues could allow remote code execution, au…
![Qualcomm fixed three zero-days exploited in limited, targeted attacks - RapidAPI]()
Qualcomm fixed three zero-days exploited in limited, targeted attacksQualcomm addressed three zero-day vulnerabilities that, according to the company, have been exploited in limited, targeted attacks in the wild. Qualcomm has shipped security updates to address three zero-day vulnerabilities that it said have been exploited in…
![ConnectWise suffered a cyberattack carried out by a sophisticated nation state actor - RapidAPI]()
ConnectWise suffered a cyberattack carried out by a sophisticated nation state actorConnectWise detected suspicious activity linked to a nation-state actor, impacting a small number of its ScreenConnect customers. ConnectWise revealed it had detected suspicious activity linked to an advanced nation-state actor. The company confirmed that the…
![A cyberattack hit hospitals operated by Covenant Health - RapidAPI]()
A cyberattack hit hospitals operated by Covenant HealthA cyberattack hit three hospitals operated by Covenant Health, forcing them to shut down all systems to contain the incident. Three hospitals run by Covenant Health were hit by a cyberattack, prompting them to shut down all their systems to contain the securi…
![Over 80,000 servers hit as Roundcube RCE bug gets rapidly exploited - RapidAPI]()
Over 80,000 servers hit as Roundcube RCE bug gets rapidly exploitedA critical remote code execution (RCE) vulnerability in Roundcube was exploited days after patch, impacting over 80,000 servers. Threat actors exploited a critical remote code execution (RCE) flaw in Roundcube, tracked as CVE-2025-49113, just days after the p…
![App Store Security: Apple stops $2B in fraud in 2024 alone, $9B over 5 years - RapidAPI]()
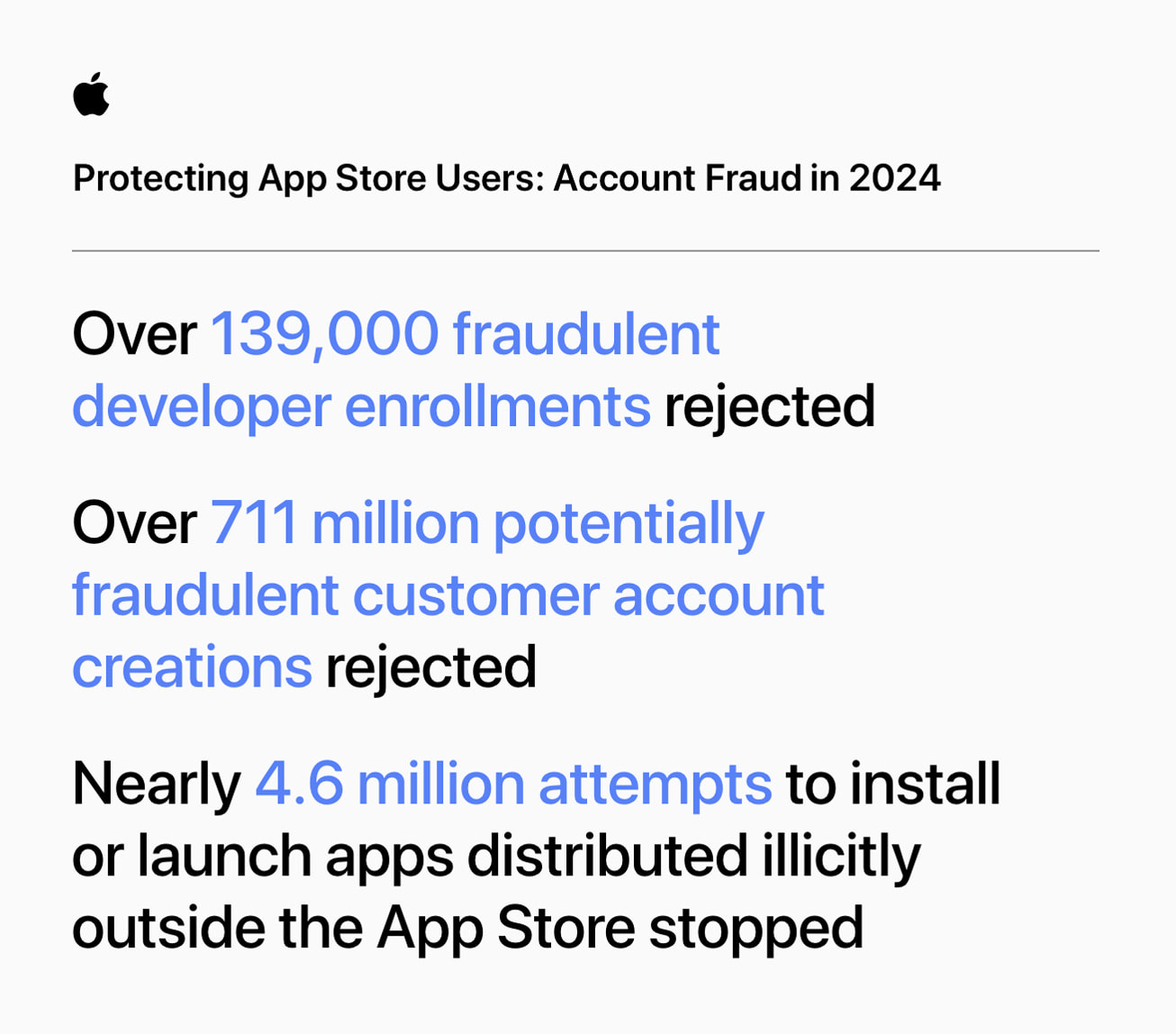
App Store Security: Apple stops $2B in fraud in 2024 alone, $9B over 5 yearsApple blocked over $9B in fraud in 5 years, including $2B in 2024, stopping scams from deceptive apps to fake payment schemes on the App Store. In the past five years alone, Apple says it has blocked over $9 billion in fraudulent transactions, more than $2 bi…
![China-linked APT41 used Google Calendar as C2 to control its TOUGHPROGRESS malware - RapidAPI]()
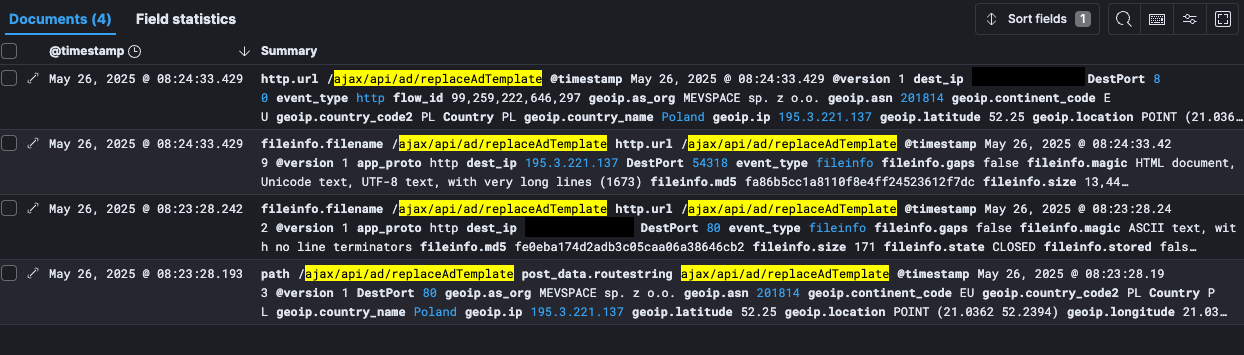
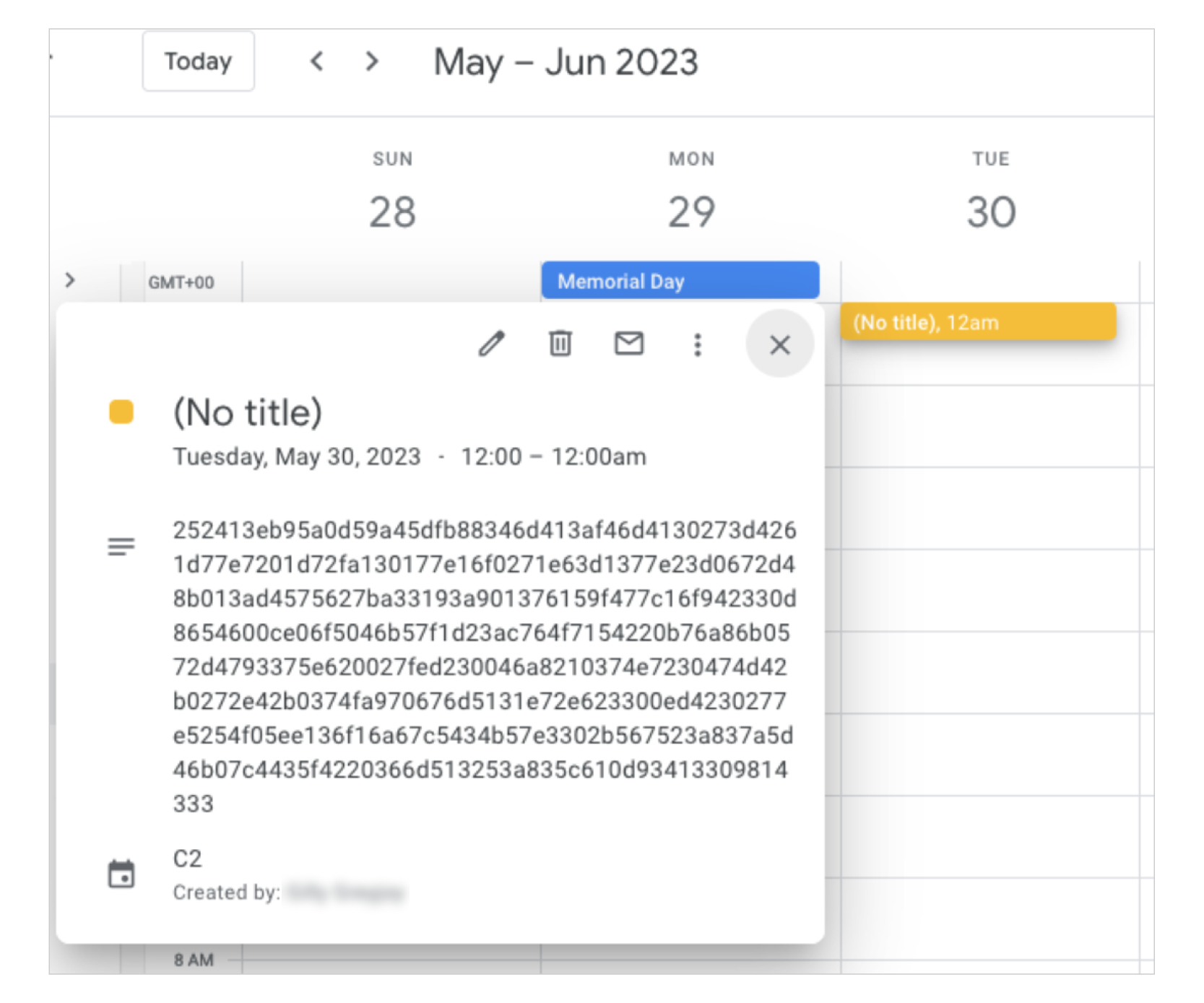
China-linked APT41 used Google Calendar as C2 to control its TOUGHPROGRESS malwareGoogle says China-linked group APT41 controlled malware via Google Calendar to target governments through a hacked site. Google warns that China-linked APT41 used TOUGHPROGRESS malware with Google Calendar as C2, targeting various government entities via a co…
![Roundcube Webmail under fire: critical exploit found after a decade - RapidAPI]()
Roundcube Webmail under fire: critical exploit found after a decadeA critical flaw in Roundcube webmail, undetected for 10 years, allows attackers to take over systems and execute arbitrary code. A critical flaw, tracked as CVE-2025-49113 (CVSS score of 9.9) has been discovered in the Roundcube webmail software. The vulnerab…
Source: NewsAPI