This product public API was created by ConnectWise. The Connectwise Control API endpoint is located at https://www.connectwise.com/. You can find the ConnectWise portal / hompage here. If you need Connectwise Control API support, you can reach out to their Twitter account at @connectwise. The Connectwise Control API requires Custom authentication. For more information, check out their API Documentation. The Connectwise Control API is not currently available on the RapidAPI marketplace.
Click "Request this API on RapidAPI" to let us know if you would like to access to this API.
Meanwhile, you can check out the top APIs that currently available for developers.
Related Articles
Related Connectwise Control API Articles
![Iran confirmed it shut down internet to protect the country against cyberattacks - RapidAPI]()
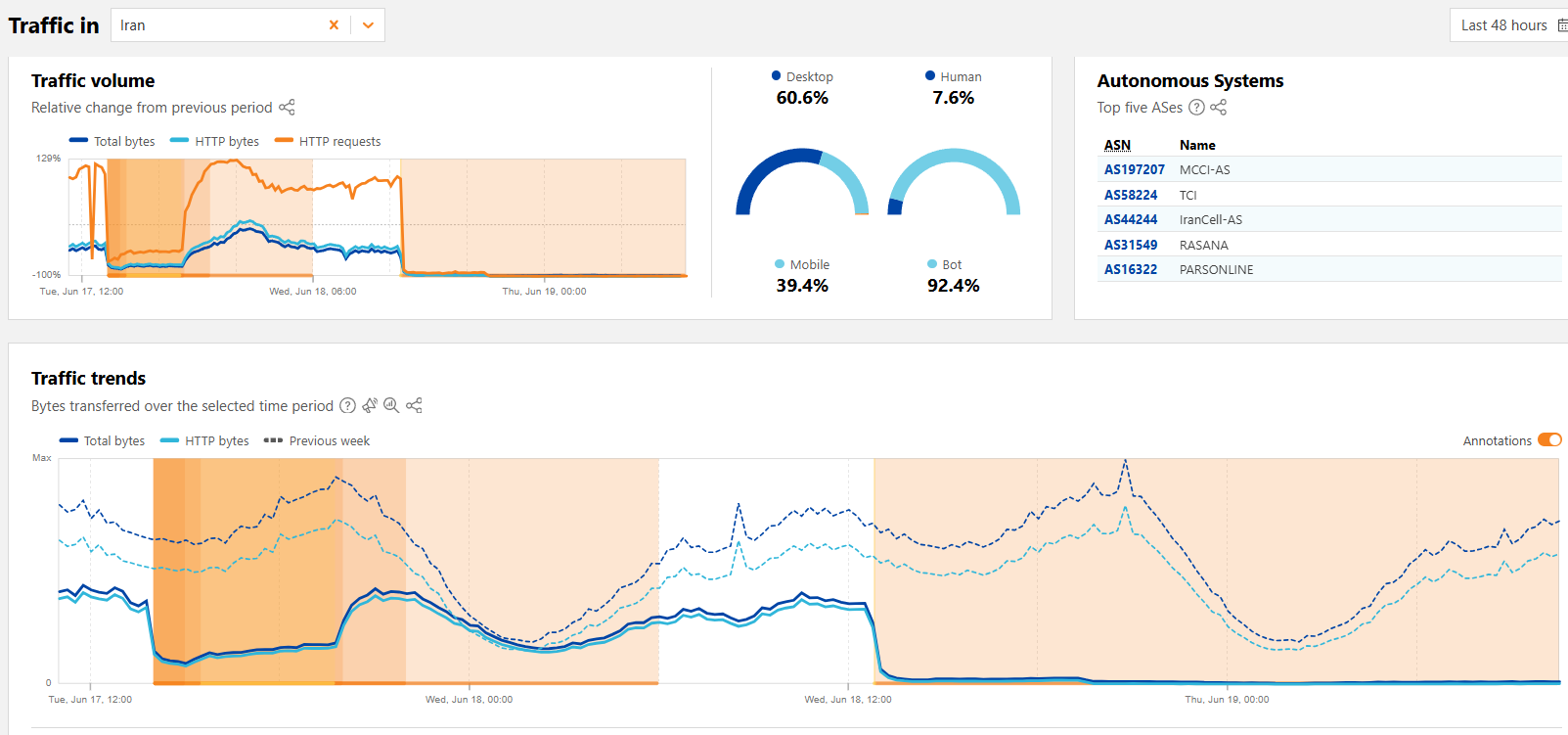
Iran confirmed it shut down internet to protect the country against cyberattacksIran confirmed an Internet shutdown to counter Israeli cyberattacks, citing threats to critical infrastructure, and interfere with drone control. Iran experienced a near-total internet blackout on Wednesday as tensions with Israel escalated into the first wee…
![China-linked group Salt Typhoon breached satellite firm Viasat - RapidAPI]()
China-linked group Salt Typhoon breached satellite firm ViasatChina-linked APT Typhoon has reportedly targeted satellite firm Viasat, the group has breached multiple telecom providers in the past. China-linked APT group Salt Typhoon hacked the satellite communications firm Viasat, the cyber-espionage group has previousl…
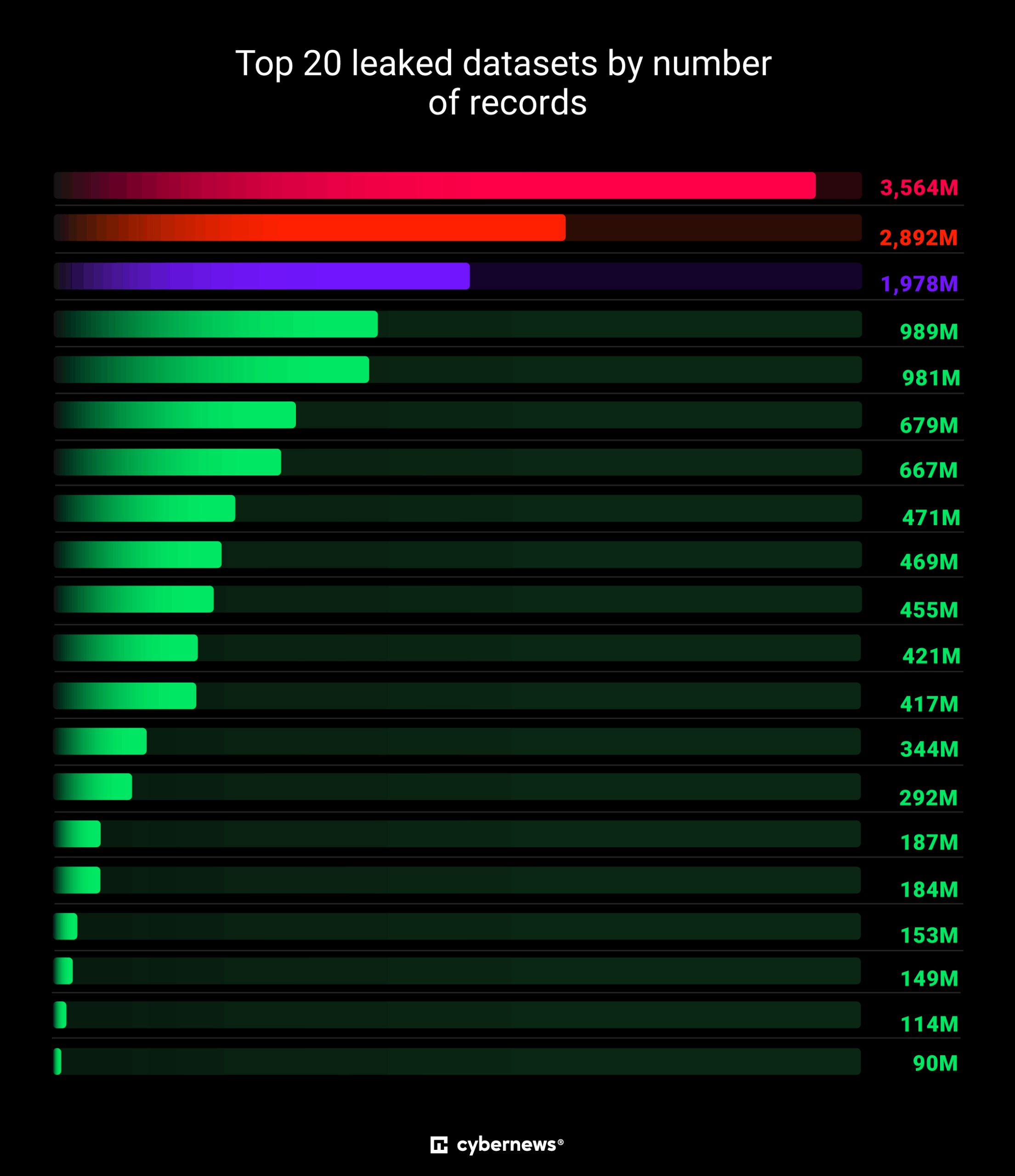
![Researchers discovered the largest data breach ever, exposing 16 billion login credentials - RapidAPI]()
Researchers discovered the largest data breach ever, exposing 16 billion login credentialsResearchers discovered the largest data breach ever, exposing 16 billion login credentials, likely due to multiple infostealers. Researchers announced the discovery of what appears to be the largest data breach ever recorded, with an astonishing 16 billion lo…
![SECURITY AFFAIRS MALWARE NEWSLETTER ROUND 50 - RapidAPI]()
SECURITY AFFAIRS MALWARE NEWSLETTER ROUND 50Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape Critical Langflow Vulnerability (CVE-2025-3248) Actively Exploited to Deliver Flodrix Botnet Predator Still Active, with Ne…
![Security Affairs newsletter Round 529 by Pierluigi Paganini – INTERNATIONAL EDITION - RapidAPI]()
Security Affairs newsletter Round 529 by Pierluigi Paganini – INTERNATIONAL EDITIONA new round of the weekly Security Affairs newsletter has arrived! Every week, the best security articles from Security Affairs are free in your email box. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press. Iran con…
![Iran-Linked Threat Actors Cyber Fattah Leak Visitors and Athletes’ Data from Saudi Games - RapidAPI]()
Iran-Linked Threat Actors Cyber Fattah Leak Visitors and Athletes’ Data from Saudi GamesCyber Fattah leaked thousands of records on athletes and visitors from past Saudi Games, per U.S.-based cybersecurity firm Resecurity. Resecurity (USA) identified the threat actors associated with the “Cyber Fattah” movement leaked thousands of records contai…
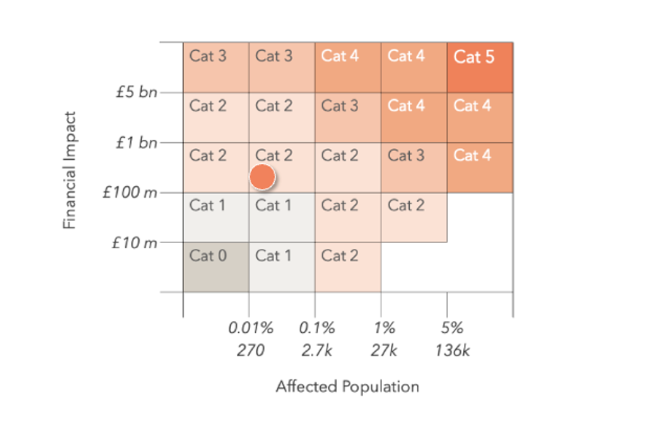
![The financial impact of Marks & Spencer and Co-op cyberattacks could reach £440M - RapidAPI]()
The financial impact of Marks & Spencer and Co-op cyberattacks could reach £440MUK’s Cyber Monitoring Centre (CMC) labels Marks & Spencer and Co-op cyberattacks a Category 2 event, estimating financial impact at £270M–£440M. The Cyber Monitoring Centre (CMC) has labeled the recent cyberattacks on Marks & Spencer and Co-op as a Category 2…
![Linux flaws chain allows Root access across major distributions - RapidAPI]()
Linux flaws chain allows Root access across major distributionsResearchers discovered two local privilege escalation flaws that could let attackers gain root access on systems running major Linux distributions. Qualys researchers discovered two local privilege escalation (LPE) vulnerabilities, an attacker can exploit the…
![Iran experienced a near-total national internet blackout - RapidAPI]()
Iran experienced a near-total national internet blackoutIran experienced a near-total internet blackout on Wednesday as tensions with Israel escalated into the first week of conflict. Global internet monitor NetBlocks reported almost near-total Internet disruptions in Iran as tensions with Israel escalated into th…
![A ransomware attack pushed the German napkin firm Fasana into insolvency - RapidAPI]()
A ransomware attack pushed the German napkin firm Fasana into insolvencyA cyberattack pushed the German napkin firm Fasana into insolvency, likely worsening existing financial troubles and serving as the final blow. German napkin maker Fasana filed for insolvency after a major cyberattack on May 19 paralyzed its systems, halting …
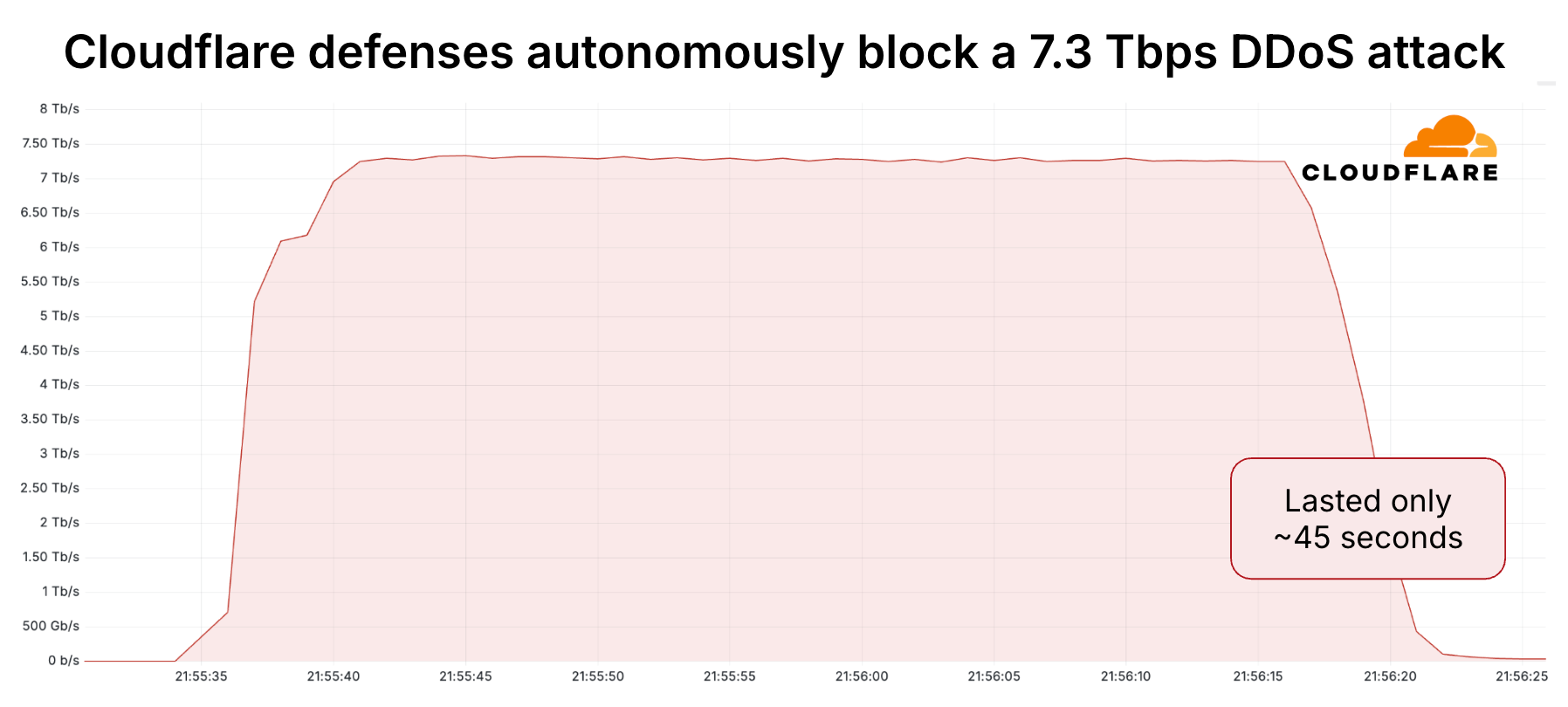
![Cloudflare blocked record-breaking 7.3 Tbps DDoS attack against a hosting provider - RapidAPI]()
Cloudflare blocked record-breaking 7.3 Tbps DDoS attack against a hosting providerCloudflare blocked a record-breaking 7.3 Tbps DDoS attack in May 2025. Cloudflare blocked a record 7.3 Tbps DDoS attack in May 2025, 12% greater than its previous peak and 1 Tbps greater than the attack reported by the popular cyber journalist Brian Krebs. Th…
![RapidAPI logo]()
Vulnerability Summary for the Week of July 7, 2025High Vulnerabilities
PrimaryVendor -- Product Description Published CVSS Score Source Info Radiflow--iSAP Smart Collector The device has two web servers that expose unaut… Source: NewsAPI
Related Connectwise Control API Videos

administrator